Private Link Generation
The Private Link Generation feature within our Face capture system empowers clients to seamlessly create secure links for initiating and overseeing customer verification processes. This process ensures efficient and reliable identity validation for various business needs.
Private Link Generation Use Case for Face capture
The Private Link Generation feature within our Face capture empowers clients to seamlessly create secure links for initiating and overseeing customer verification processes. This process ensures efficient and reliable identity validation for various business needs.
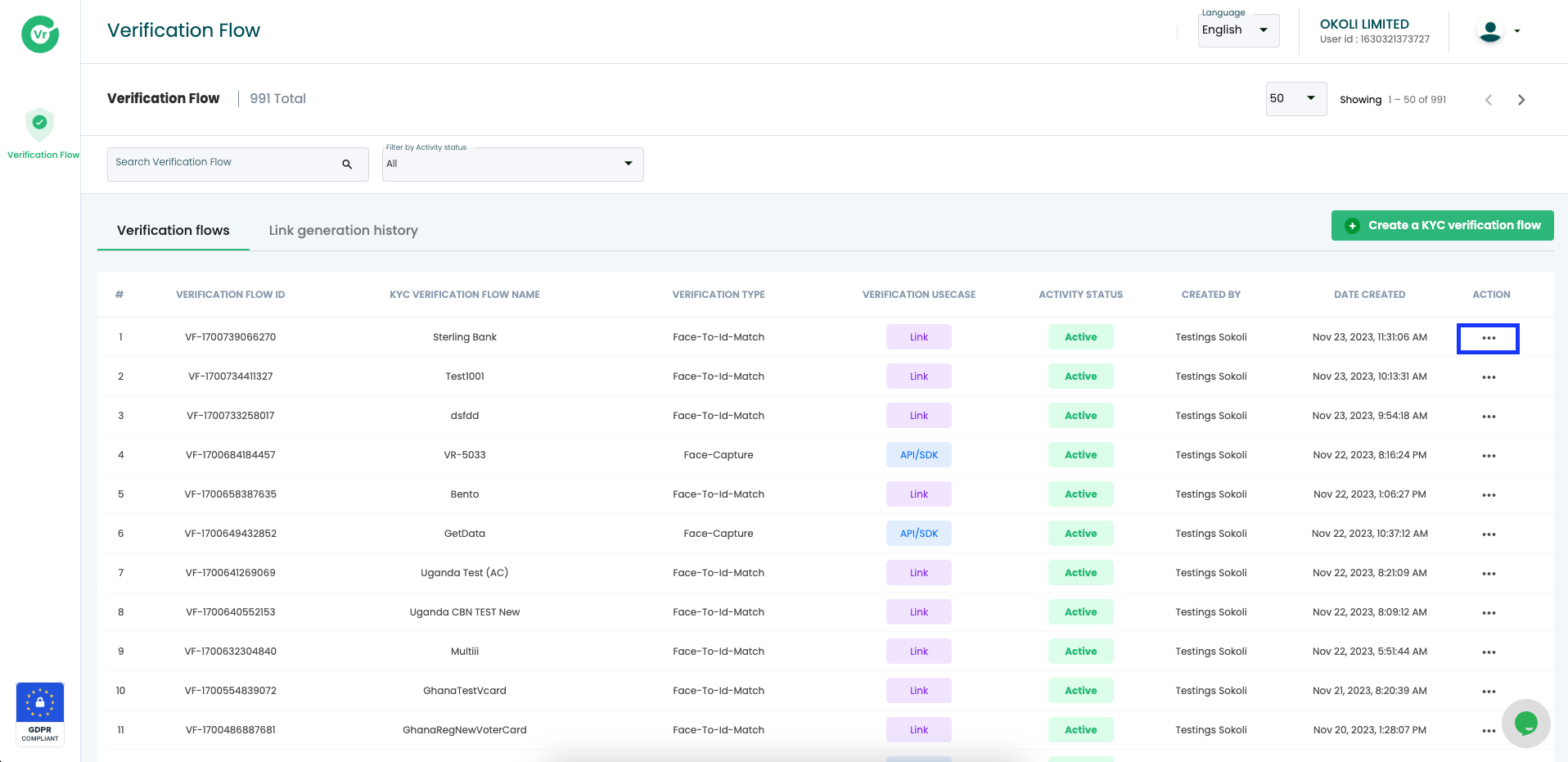
Step 1. Access Verification Flow TableNavigate to the Verification Flow Table, which serves as the centralized hub for managing all verification flows.
Step 2. Generate Secure Link
- Clients can easily generate a secure link through a straightforward process.
- Click on the "Generate Link" option to create a unique and encrypted URL for initiating the verification process.
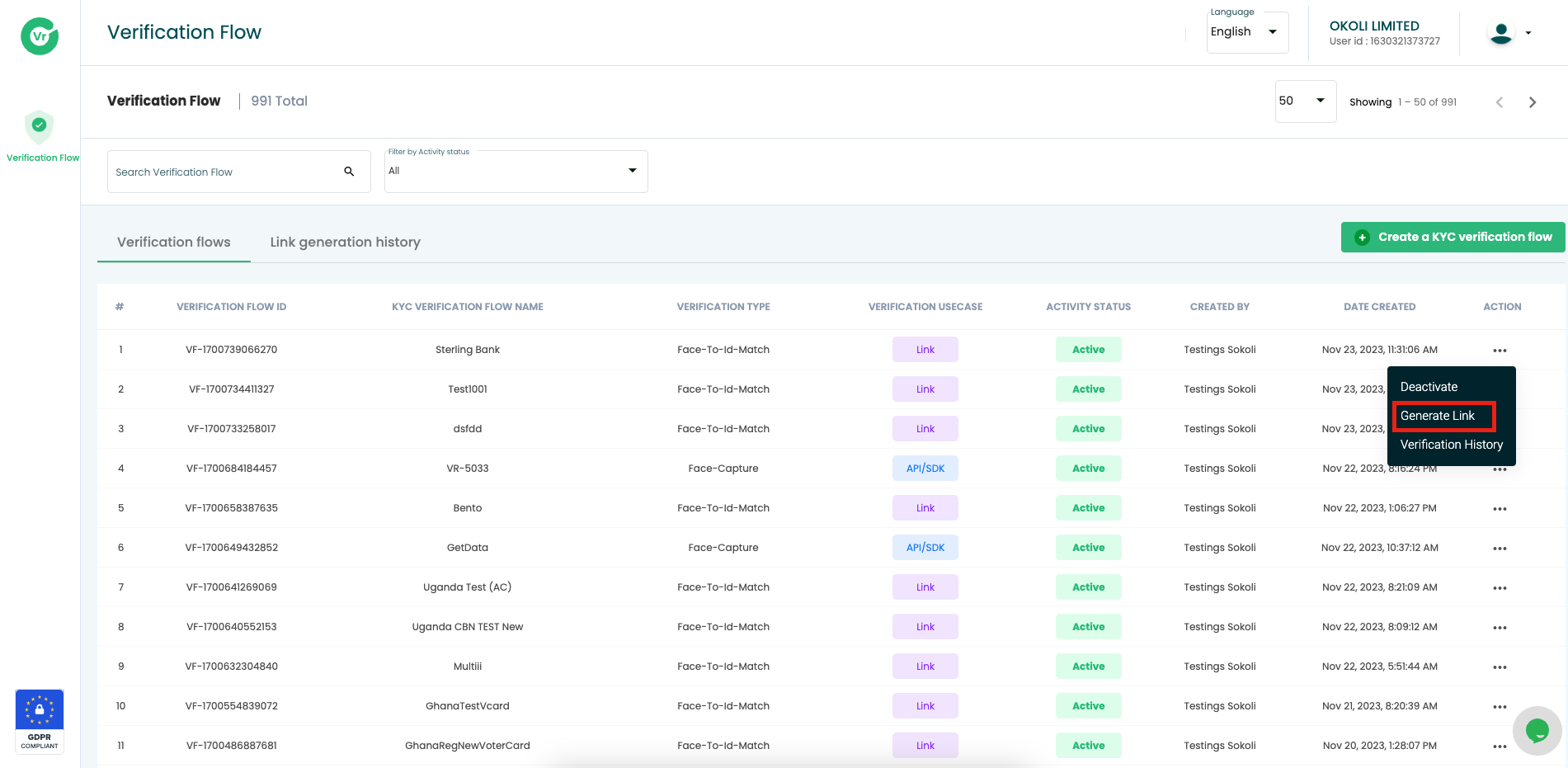
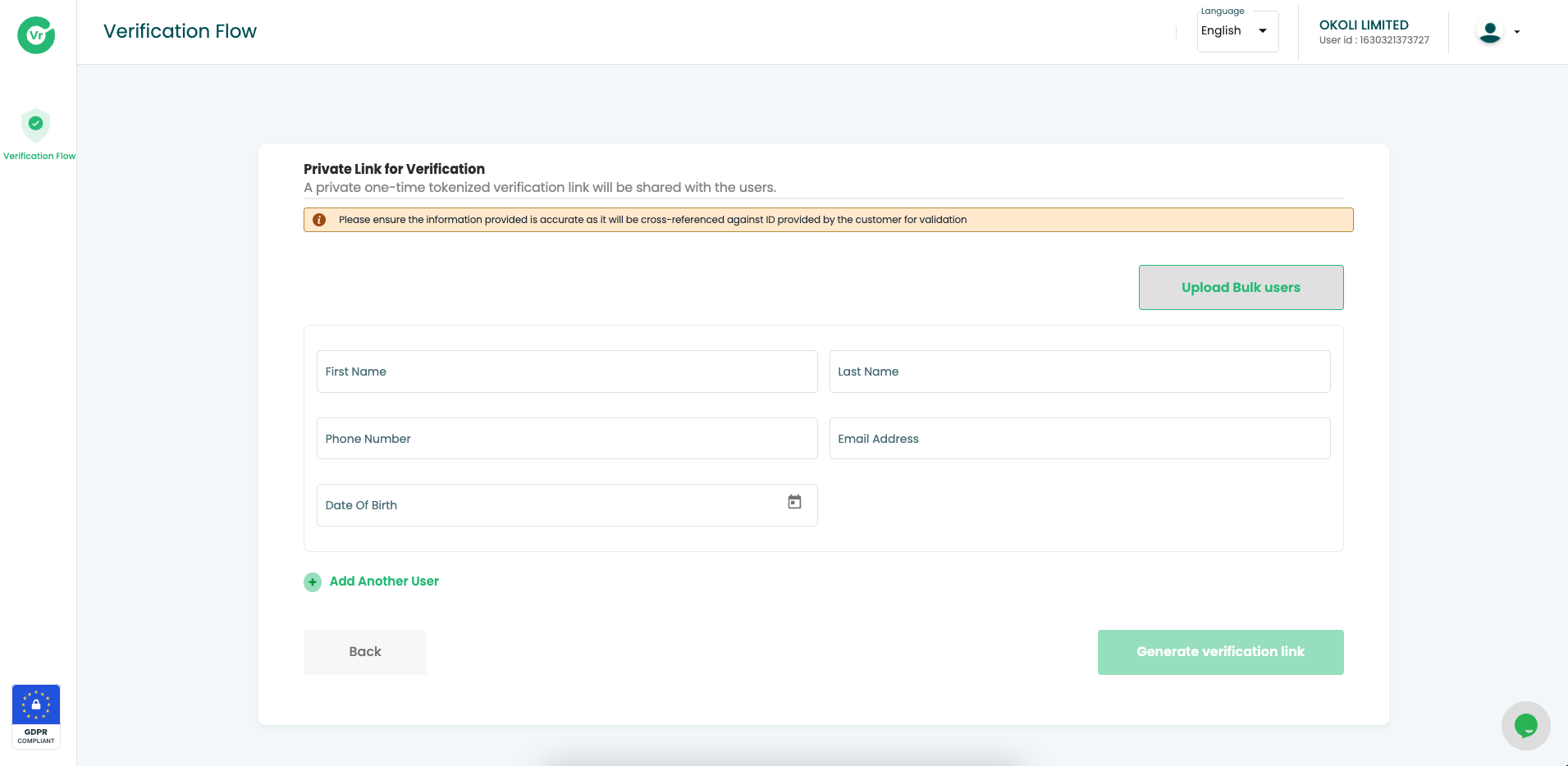
Step 3. Input Customer Details
- Enter valid and accurate customer information into the system. These details are crucial for comprehensive customer profile validation.
- Ensure that the information provided aligns with the necessary verification documents to ensure a smooth and accurate validation process.
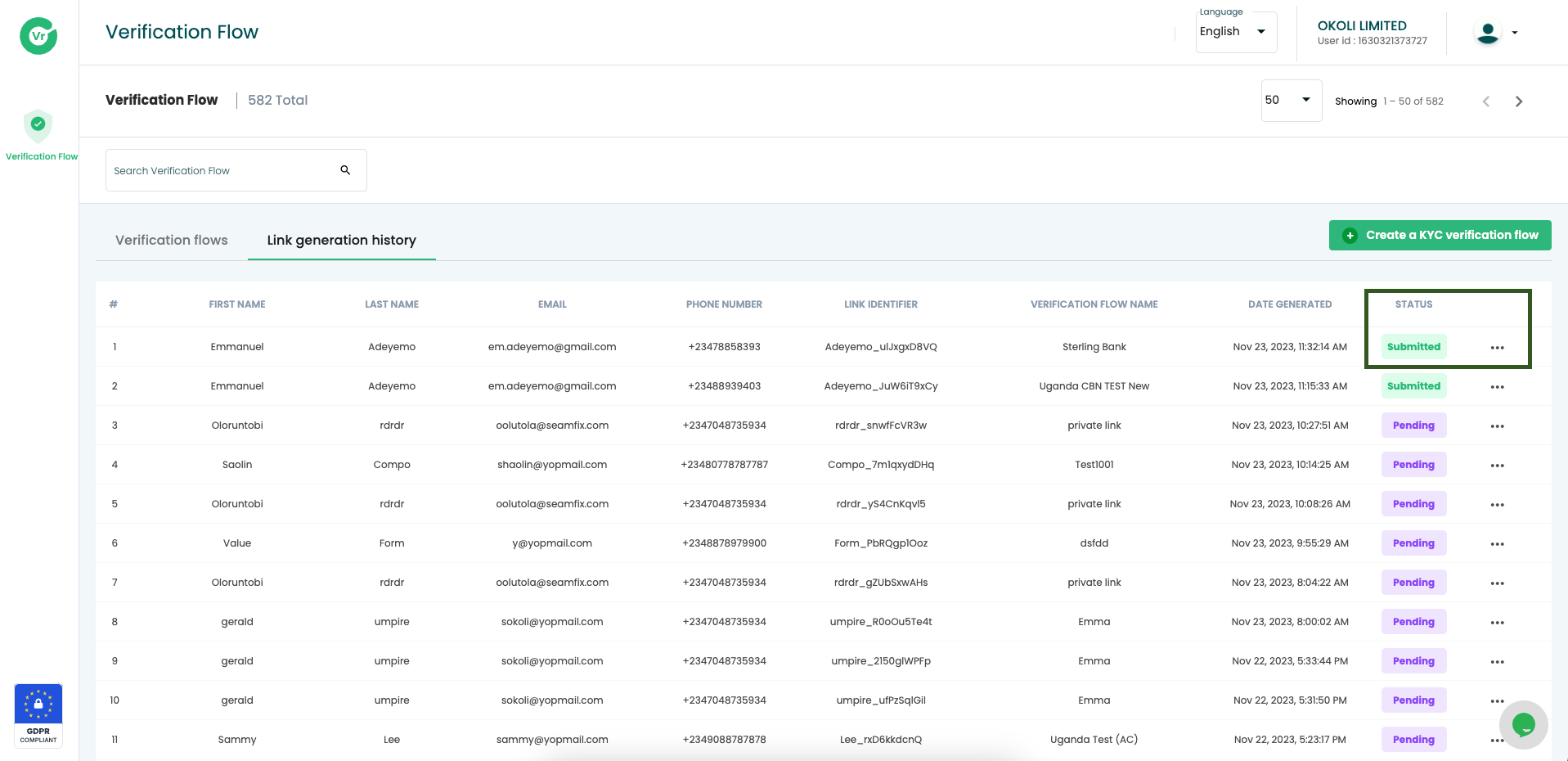
Step 4. Real-time Updates
- Access comprehensive reports summarizing the verification results.
- The "View Report" section provides in-depth insights into the verification process, including details on document validation, identity matches, and any discrepancies found.
## Benefits:
- Efficiency: Streamlined process for initiating and monitoring verification flows.
- Security: Utilization of secure, encrypted links for protecting customer data.
- Transparency: Real-time updates ensure clients are informed at every stage of the verification process.
- Insightful Reports: Detailed reports offer comprehensive insights into verification results.
Use Case Scenario:Sarah, a compliance officer at a financial institution, logs into the Face capture system. She accesses the Verification Flow Table, generates a secure link for a new customer's identity verification, inputs the necessary details, and monitors the process via real-time updates. Upon completion, she reviews the detailed report to ensure compliance with regulatory requirements.
Conclusion:
The Private Link Generation feature for Face capture provides a robust solution for clients to initiate, manage, and monitor capture identity verification process efficiently, securely, and with comprehensive insights.
Updated 5 months ago
